Ransomware
Ransomware is malware designed to encrypt files on a device, rendering files and the systems that rely on them unusable. Attackers typically demand ransom in exchange for a decryption key and/or to prevent sensitive data being leaked or sold on the internet.
2021 was notable for serious attacks against critical infrastructure, including the Colonial Pipeline attack, the attack on the IT systems of the Italian region of Lazio, a supply chain attack on MSPs who used software from Kaseya, along with a plethora of other incidents in sectors such as healthcare, pharmaceuticals, education, food distribution and public services. Ireland was not immune to this surge of ransomware incidents, with a hugely disruptive ransomware attack being carried out on the healthcare system in May 2021.
No attack is exactly the same, and there are steps that occur both before and after the attack itself, however, a ransomware attack broadly follows three key steps: gaining Access, preparation, and impact.
Breaking the Ransomware Attack Chain
No attack is exactly the same, and there are steps that occur both before and after the attack itself, however, a ransomware attack broadly follows three key steps: Gaining access, Preparation, and Impact. There are many opportunities throughout the Ransomware Attack Chain, whereby good cybersecurity practices will allow you to stop an attacker and #BreaktheChain. Check out our infographic that represents the priority actions you can take. Further guidance on ransomware can be found here: NCSC Quick Guide to Ransomware.
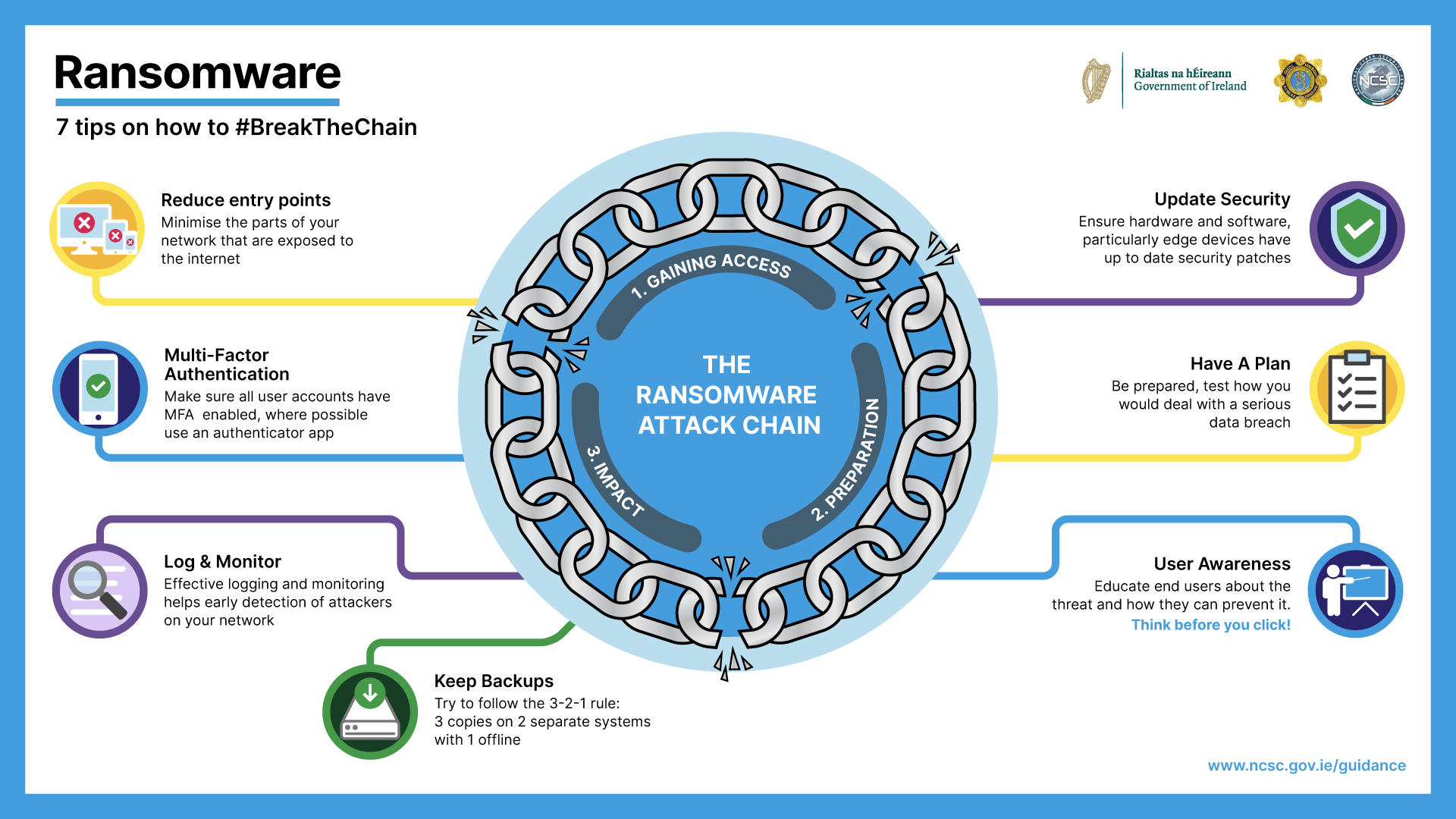
Attackers are scanning your attack surface, make sure you understand it well. Make sure you minimise the parts of your network that are exposed to the internet by keeping edge devices to a minimum and closing unused ports and protocols. This reduces the entry points for attackers.
Conduct vulnerability scanning and make sure all of your hardware and software, particularly edge devices, are kept up to date with the latest security patches. This prevents attackers exploiting known vulnerabilities to access the network, moving laterally and escalating their privileges.
Make sure all remote access and privileged user accounts have MFA enabled. This makes it more difficult for an attacker to use stolen credentials. Where possible, avoid SMS as the second factor, and instead use an authenticator app.
By implementing effective logging and monitoring you will be able to detect attackers on your network and take action to remove them from the network. It will also allow you to understand what has happened and in turn, aid in the recovery process.
Make sure you keep backups of all of your data. Try to follow the 3-2-1 rule – 3 copies, on 2 separate systems, with 1 being ‘offline’. This will allow you to restore if your data is encrypted.
Make sure you have a plan for what you will do if you are attacked. It should include key actions to take and people to contact. Test the plan! This will allow you to contain and effectively remediate a ransomware incident. You should also rehearse how you would deal with a serious data breach – a good response to a data breach is crucial for your reputation.
Finally - make sure you educate all your users about the threat of ransomware and how they can prevent it. This will help reduce the chances of a user being tricked by phishing. A well-educated workforce is key to preventing and responding well to incidents.
Ransomware operators are not only interested in critical infrastructure, ransomware attacks can affect all types of organisations, both large and small. The Ransomware Quick Guide is for organisations to understand the steps in a Ransomware Attack Chain, and more importantly how good cybersecurity practices will allow you to stop an attacker and #BreakTheChain.
Please see our guidance section for additional resources.

