Active Malware Distribution Sites
The URLhaus Project
The URLhaus project, was launched by abuse.ch in 2018, to provide a platform where security researchers can exchange information on sites that are being used or exploited for the distribution of malware. In 2019, it was reported that 265 security researchers had contributed to and used the URLhaus platform to report sites that were being exploited for the distribution of malware.
The project maintains a depository of sites reported as having been exploited, or used for the distribution of malware. The URLhaust dataset is updated every five (5) minutes and contains the malicious Uniform Resource Locators (URLs) of sites that are either actively distributing malware or that have been added to the URLhaus dataset within the past 90 days.
CSIRT-IE monitors the URLhaus dataset for reports of sites, within its jurisdiction, that are reported to be actively distributing malware.
Active Malware Distribution Sites
The URLhaus platform only report sites (URLs) that are directly being used to distribute malware. This means that the malware distribution site are currently serving a payload. A payload can be any file, such as an executable, a script or a document that can infect or harm a computer once downloaded and executed.
Examples of executables, scripts and documents that can harm or infect a computer.
| No. | Payload | Description |
|---|---|---|
| 1. | Microsoft Windows Executables | A file that contains binary machine code that has been compiled from source code. When the executable file is triggered by a user or an event, the computer executes the code, that the file contains. |
| 2. | Microsoft Office Documents | The three main types of file formats in the Microsoft Office Application suite are Word, Excel and PowerPoint. Any of these file formats may be used to deliver malware. |
| 3. | PowerShell scripts | PowerShell is an object-oriented scripting language developed by the Microsoft Corporation, designed for system administration. PowerShell can be embedded in other applications. |
| 4. | Bash scripts | A Bash script is a plain text file which contains a series of commands. These commands are read and executed by the bash script line by line. |
| 5. | HTA | HTML Application (HTA) is a Microsoft Windows program whose source code consists of HTML, Dynamic HTML and one or more scripting languages supported by Internet Explorer, such as VBScript or JScript. The HTML is used to generate the user interface, and the scripting language is used for the program logic. Used as droppers for malware in the wild. |
| 6. | ELF | Executable and Linkable Format (ELF), is the standard file format for all the binaries compiled on a NIX systems (i.e UNIX based systems such as Linux). The ELF infection method is based on utilising the page padding on the end of the text segment which provides suitable hosting for malicious code. |
Note: Adware & Phishing kits are not Malware, and are not reported on the URLhaus platform.
Active Malware Distribution Sites Report
In the event of receiving an e-mail, Active Malware Distribution Site(s) Report, from CSIRT-IE, recipients are advised to view the attached file:- events.csv
Contained within the file, is the following information:-
CSIRT-IE Report of Active Malware Distribution Sites:- events.csv
| No. | Column Name | Description |
|---|---|---|
| 1. | IP Address | The Internet Protocol (IP) address of the affected host. | 2. | Hostname | The hostname of the affected domain or host. |
| 3. | URL: | The Uniform Resource Locator (URL) of the affected site. | 4. | Proof_URLhaus | Link to the URLhaus database entry of the reported site. |
| 5. | Timestamp | Date and Time site was reported to the URLhaus Project. |
URLhaus database entry for reported site.
Recipients of an Active Malware Distribution Sites Report, can access and view information, contained in the URLhaus database, on the reported site, by accessing the URL link, contained in the Proof URLhaus column of the file events.csv.
Example of URLhaus Database entry for a reported site.
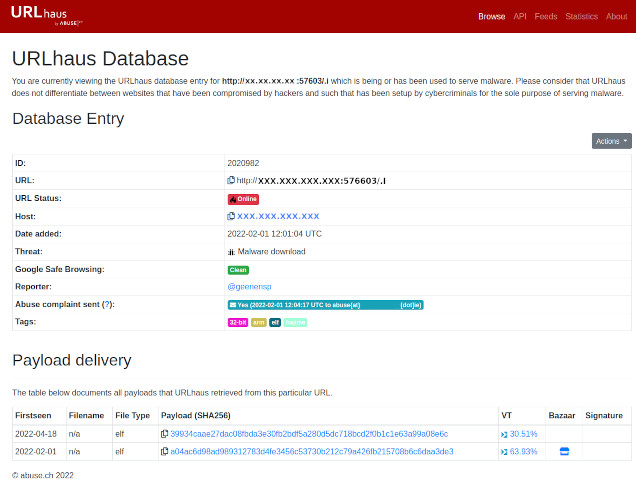
URLhaus database - Database entry - Index
| No. | Column Name | Description |
|---|---|---|
| 1. | ID: | URLhaus database Identification Number (ID) of the entry for the reported site. |
| 2. | URL: | The Uniform Resource Locator (URL) of the site reported to be actively distributing malware. |
| 3. | URL Status | The URL Status of the reported site - Color red indicate site is online and actively distributing malware. Color green indicates site is offline and no longer distributing malware. |
| 4. | Host | The Internet Protocol (IP) address of the host responsible for hosting the reported site. |
| 5. | Date added | Date the URL was added to the URLhaus database. |
| 6. | Threat | The threat posed by the site reported. e.g. Malware download. |
| 7. | Google Safe Browsing | Google Safe Browsing is a service provided by Google Inc., which alert users when they attempt to navigate to a dangerous site or to download a dangerous file. Warnings from various Anti-Virus vendors and Blacklist providers, such as, Spamhaus DBL, SURBL (Spam URI RBL), Quad9, AdGuard and Cloudflare may be included in the URLhaus database entry for the reported site, in the event they have reported the site to be clean or otherwise. |
| 8. | Reporter | The twitter account of the security researcher or threat analyst that reported the site for malware distribution. |
| 9. | Abuse complaint sent (?) | Date and time, complaint was sent to the abuse contact of the site reported. |
| 10. | Takedown time: | Time taken, from when the site was first reported, to when the site was taken offline. |
| 11. | Tags: | The various tags associated with the file payload distributed by the reported site. |
URLhaus database - Payload Delivery - Index
| No. | Column Name | Description |
|---|---|---|
| 1. | Firstseen | Date file was first reported. |
| 2. | Filename | The name of the file. |
| 3. | File Type | The File type - elf - Executable and Linkable Format is the standard format for all the binaries compiled on a NIX system (i.e. UNIX based system such as Linux). |
| 4. | Payload (SHA256) | SHA256 256 bits hash value of the payload file. |
| 5. | VT | The total number of VirusTotal partners who consider the reported site harmful. Note: 10 security vendors and 1 sandbox flagged this file as malicious (11) out of the total number of partners who reviewed the file (In this case, 36). |
| 6. | Bazaar | An icon in this box, indicates there is a sample of the file payload on the MalwareBazaar platform. The MalwareBazaar platform attempts to identify if the sample provided is malicious or not. |
| 7. | Signature | The Digital Signature of the file. |
URLhaus database - Actions options.
Solution
Constituents are advised to investigate the reported site, and to render it harmless, if necessary.
Constituents, on completion of their investigation and subsequent actions, are requested to update the 'Actions' option of the URLhaus database Entry, for the reported site.
In the event that the report was accurate, constituents are advised to take appropriate measures to secure the site and to monitor the site for attempts of reinfection.
